The worth proposition for the companies in the EM+S E5 suite does not appear like it has been convincing to consumers for a though now. Around the previous 12 months or so, Microsoft has been placing a great deal of get the job done into the Defender solutions to boost that value proposition, and to present a much better technological protection option for Microsoft 365 consumers.
In the very last year or so Microsoft has rebranded and reorganized the Defender applications into Defender for Cloud Apps, Defender for Office 365, Defender for Endpoint, and Defender for Id. Even though people 4 solutions are a fantastic start out, there are however gaps in the safety they offer.
To that finish, Microsoft has extra a new product in public preview to the Defender Suite, Microsoft Defender Vulnerability Management (DVM). DVM is specific at enhancing vulnerability management in the subsequent parts:
- Safety baselines evaluation
- Browser extensions evaluation
- Electronic certificates assessment
- Network shares assessment
- Blocking susceptible programs
- Vulnerability assessment for unmanaged endpoints
In this site post we’re going to glimpse at the community preview for this new company. How to get it activated in your tenant, what it does, and in which I see it fitting into your all round safety architecture for Microsoft 365.
Activating the community preview
Whilst general public previews for numerous new Microsoft 365 characteristics are quickly included to tenants, the public preview for DVW necessitates a small approach to activate. You can sign up listed here. That approach only took me a few of minutes, then I experienced new licenses in my tenant that I could assign to an admin account to achieve accessibility to DVM functions. When that is comprehensive, you will have obtain to the feature we’ll go over below.
Exactly where is DVM?
The GUI for the Microsoft 365 Defender stack of purposes is mostly (but not fully) homed in the Microsoft Protection Portal. Though this can make it a little complicated to differentiate the performance of the distinct programs within the Defender stack, it also offers us a “one cease shop” for Microsoft 365 protection configurations. It’s possible a separate portal for every application would be a excellent notion, but then once again maybe this way is best.
As soon as you have DVM accredited and you have logged into the Protection Portal, you will discover all the new DVM characteristics accessible below the Endpoints section on the remaining-hand side of the display screen:
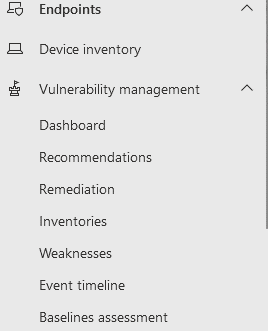
There are at the moment 7 subsections under Vulnerability Management here. As this application is nevertheless in public preview, that may perhaps alter right before DVM hits GA.
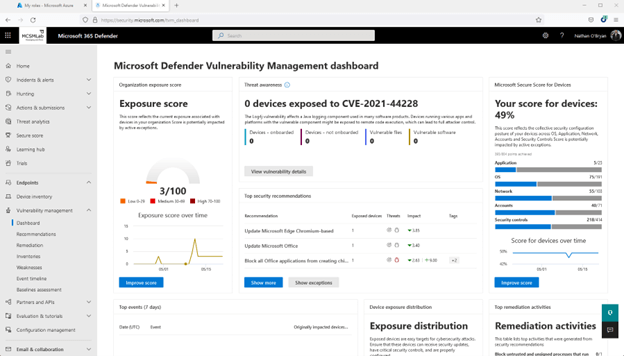
Checking out the Dashboard and Recommendations
The to start with region to take a look at is the dashboard. Right here you will locate a quick perspective of a number of distinctive steps of vulnerability within just your Microsoft 365 tenant.
In my tenant, you can see my exposure rating is small (3/100 is a fantastic thing. You want that number to be as reduced as feasible), and my secure rating for devices isn’t terrific (49% signifies I have remediated about fifty percent of the challenges Microsoft monitors to make up that rating).
Clicking on Increase Rating on either of individuals widgets will take you to the suggestions sub-part, wherever advised remediations are in-depth to assistance you enhance the stability posture of your tenant.
Below is a screenshot of the recommendations website page for my unit safe rating. With 61 merchandise to tackle, it seems like I have to some get the job done to do in my tenant.
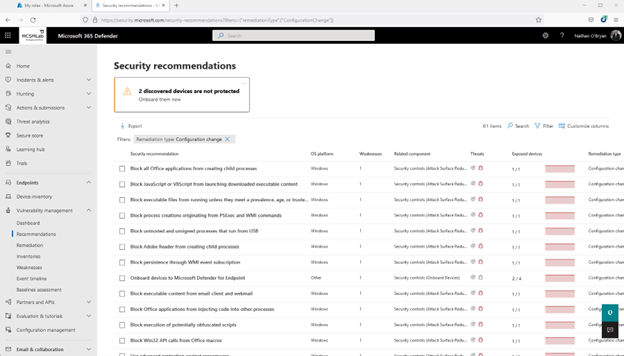
Remediation
The remediation sub-section is for arranging the suggestions into active tasks.
Going back up to suggestions for my secure score for units, I picked one particular of the tips (in this case “Update Office”), and then selected the Ask for remediation button at the base of the fly-out web page.
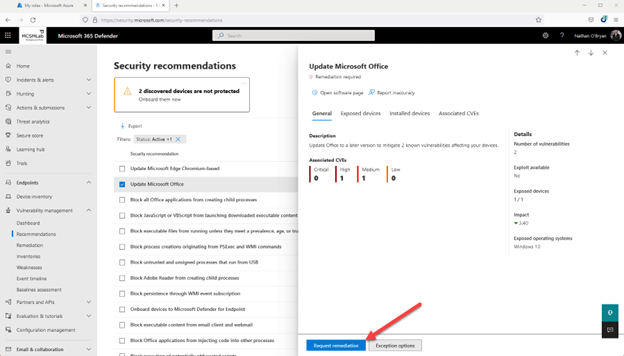
This will give you a rapid wizard that will allow you to mark that advice for remediation. It is by no suggests a comprehensive-blown ticketing technique, but this appears to be like it could be useful for prioritizing the implementation of individuals suggestions in your team. Not super beneficial for me, as I am the only administrator in my tenant.
Inventories
The inventories tab presents you an stock of the programs, browser extensions, and certificates installed on Home windows machines that have been inventoried into Endpoint Administration.
I do have an iPad that has Defender, but no purposes from that unit are inventoried in this article. This sub-area will stock macOS, Linux, and Home windows. iOS and Android gadgets are remaining out for now.
Weaknesses
The weaknesses sub-segment is but a further view of the very same information and facts introduced in a different way. Here you will see vulnerabilities that can have an effect on your devices listed by vulnerability name.
Beneath you can see I selected just one of the vulnerabilities that is similar to Office. It shows me that I have just one Windows 10 laptop computer that desires an Business update.
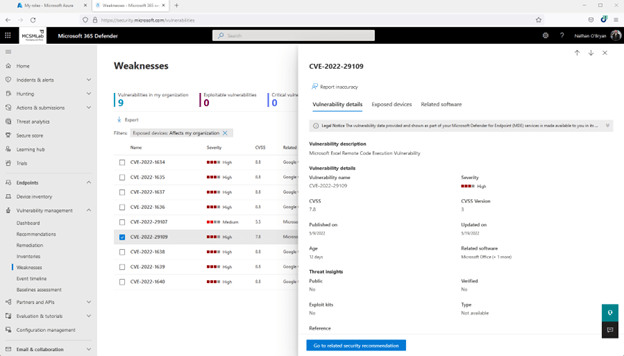
It’s telling me that updating Office on that just one laptop will take care of the Advice, the Remediation that I opened from that Advice, and this Weakness shown listed here.
When that level of redundancy most likely is not important for a smaller tenant like mine, I do look forward to taking part in all around with DVM in a substantially larger sized tenant. I think this info would be a great deal additional beneficial in a larger atmosphere in which it’s far more tricky to hold keep track of of the distinctive vulnerabilities impacting a deployment.
Celebration Timeline
Guess what is in the Function Timeline sub-area. If you guessed another look at of the exact vulnerabilities, then you just gained a gold star for the working day.
In the screenshot underneath, you can see that I definitely need to have to update Office on that notebook!
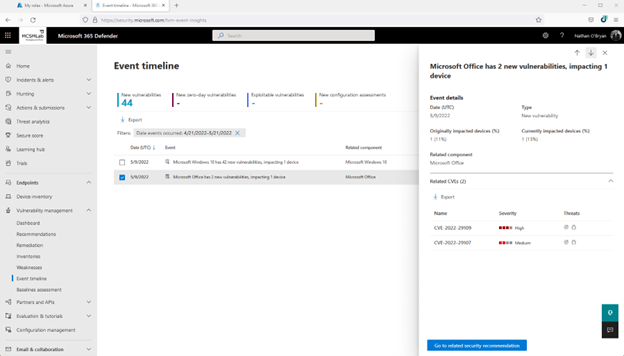
All over again, this is the exact two Business vulnerabilities that are revealed in a marginally distinct view. There is even a button here that will take you back again up to the Suggestions for these vulnerabilities.
Baseline Assessment
So much DVM has demonstrated us a dashboard that summarizes the vulnerabilities stated in the following five sub-sections, then those people very same vulnerabilities stated in those people 5 distinctive subsections. I don’t want to seem way too “complainy” right here, as this is excellent vulnerability information that can unquestionably support directors far better protected their devices, but I do assume all those sub-sections could be condensed into a solitary pane with some kind of diverse views. I am not a UI designer, so maybe there is a superior cause Microsoft felt they essential all that authentic estate within the Safety Heart to present the same data multiple situations.
The Baseline Assessment sub-section, nevertheless, does present diverse features. In accordance to Microsoft Documentation:
“A stability baseline profile is a custom made profile that you can build to assess and keep an eye on endpoints in your corporation in opposition to marketplace stability benchmarks. When you build a protection baseline profile, you happen to be generating a template that is composed of several system configuration settings and a base benchmark to assess in opposition to.”
To develop a Baseline Assessment profile:
- From the Baseline Evaluation sub-area, choose “+Create” in the higher left to create a new profile.
- Name your new profile and increase a description. Find Subsequent.
- Decide on your profile scope by picking program to keep track of (Versions of Windows 10 and 11 are outlined in this article. Hopefully Microsoft will add extra software package at a afterwards day), a baseline benchmark (I selected CIS v1.12.), and a compliance degree. Pick Subsequent
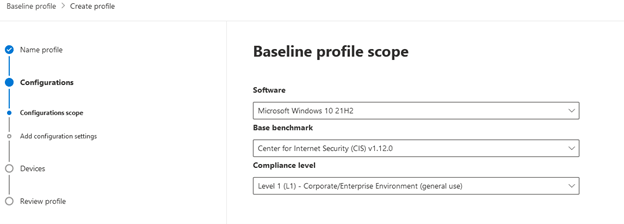
- Insert configuration options. Based on the benchmark and compliance stage chosen on the previous webpage, you will see diverse configuration settings you can choose. With the options I manufactured there are hundreds of distinct configuration options for me to select from. I’m going to pick them all for this exam profile, but you’ll want to devote some time on deciding on options that meet your organization’s compliance demands. There is also a Personalize button to the suitable of each and every placing so you can edit each setting independently. After you’re completed, decide on Up coming.
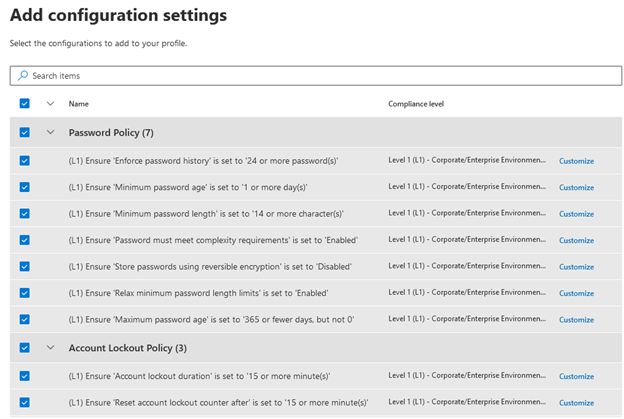
- Opt for devices to assess. I only have 1 machine in my tenant to which this profile can apply, so I selected All machine groups. Pick Future, then assessment you profile configurations on the next web site and post the profile. The moment you have submitted your bassline evaluation profile, it will take some time for any new details to show up. The documentation says 12 hours.
I’m likely to allow that run, then we’ll take a deeper look at the baseline assessment and more than DVM features in a potential blog site submit.
With electronic mail staying a person of the most mission-important resources for companies currently, how do you make sure important business enterprise conversation stays up and operating? How do you exhibit to senior administration that extra means are needed to fulfill escalating desire or that provider ranges are being fulfilled?
Formulated by Exchange architects with immediate item input from Trade MVPs, ENow’s Mailscape helps make your career easier by putting all the things you have to have into a solitary, concise OneLook dashboard, in its place of forcing you to use fragmented and difficult resources for checking and reporting. Straightforward to deploy and intuitive to use, get started off with Mailscape in minutes instead than times.
Obtain YOUR Totally free 14-Day Demo and merge all vital things for your Trade checking and reporting to preserve your messaging infrastructure up and managing like a pro!
Products HIGHLIGHTS
- Consolidated dashboard view of messaging environments overall health
- Quickly validate exterior Mail movement, OWA, ActiveSync, Outlook Everywhere
- Mail circulation queue monitoring
- DAG configuration and failover monitoring
- Microsoft Protection Patch verification
- 200+ constructed-in, customizable reviews, such as: Mailbox sizing, Mail Targeted traffic, Quota, Storage, Distribution Lists, Public Folders, Databases dimensions, OWA, Outlook variation, permissions, SLA and cell device stories